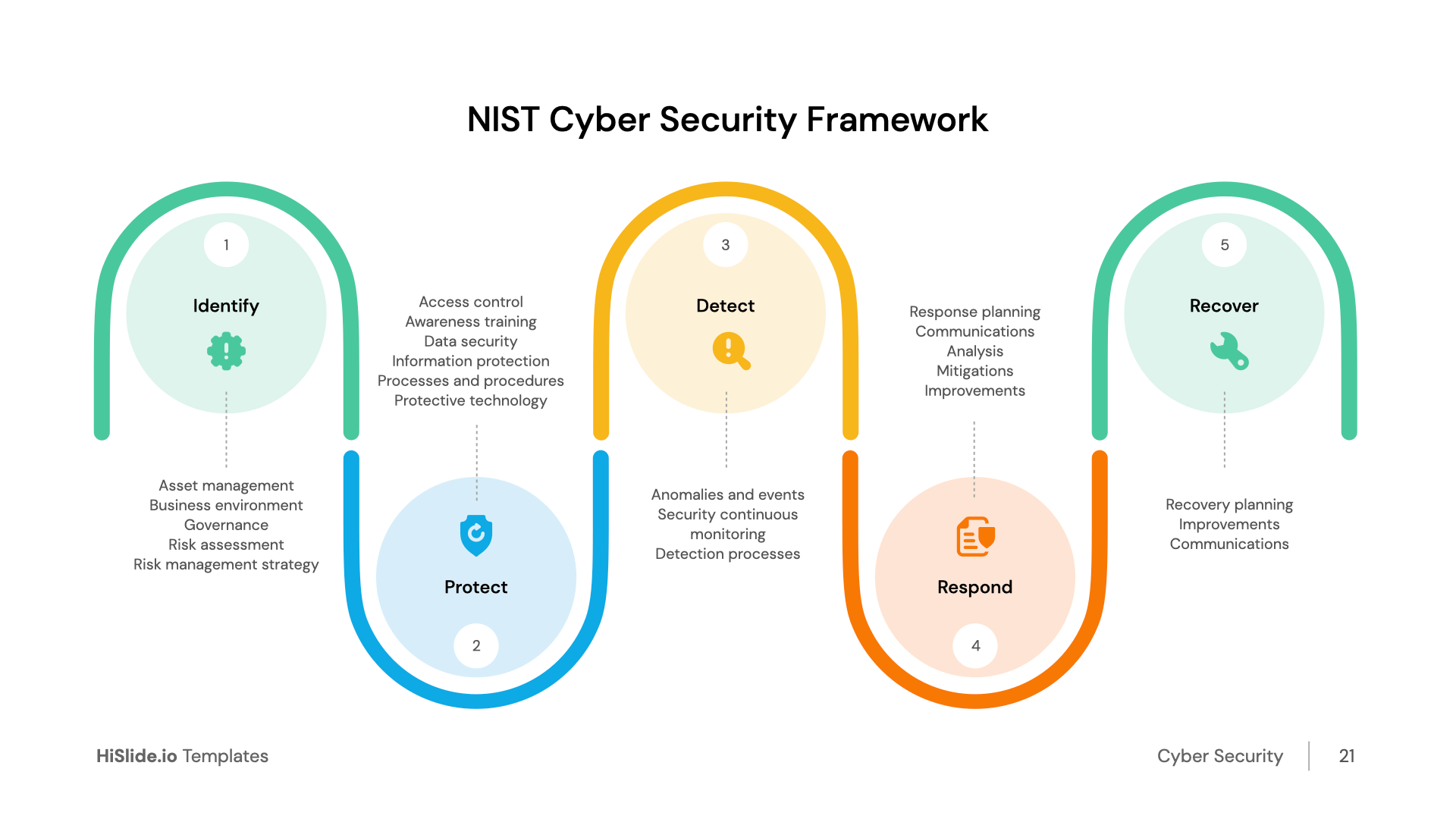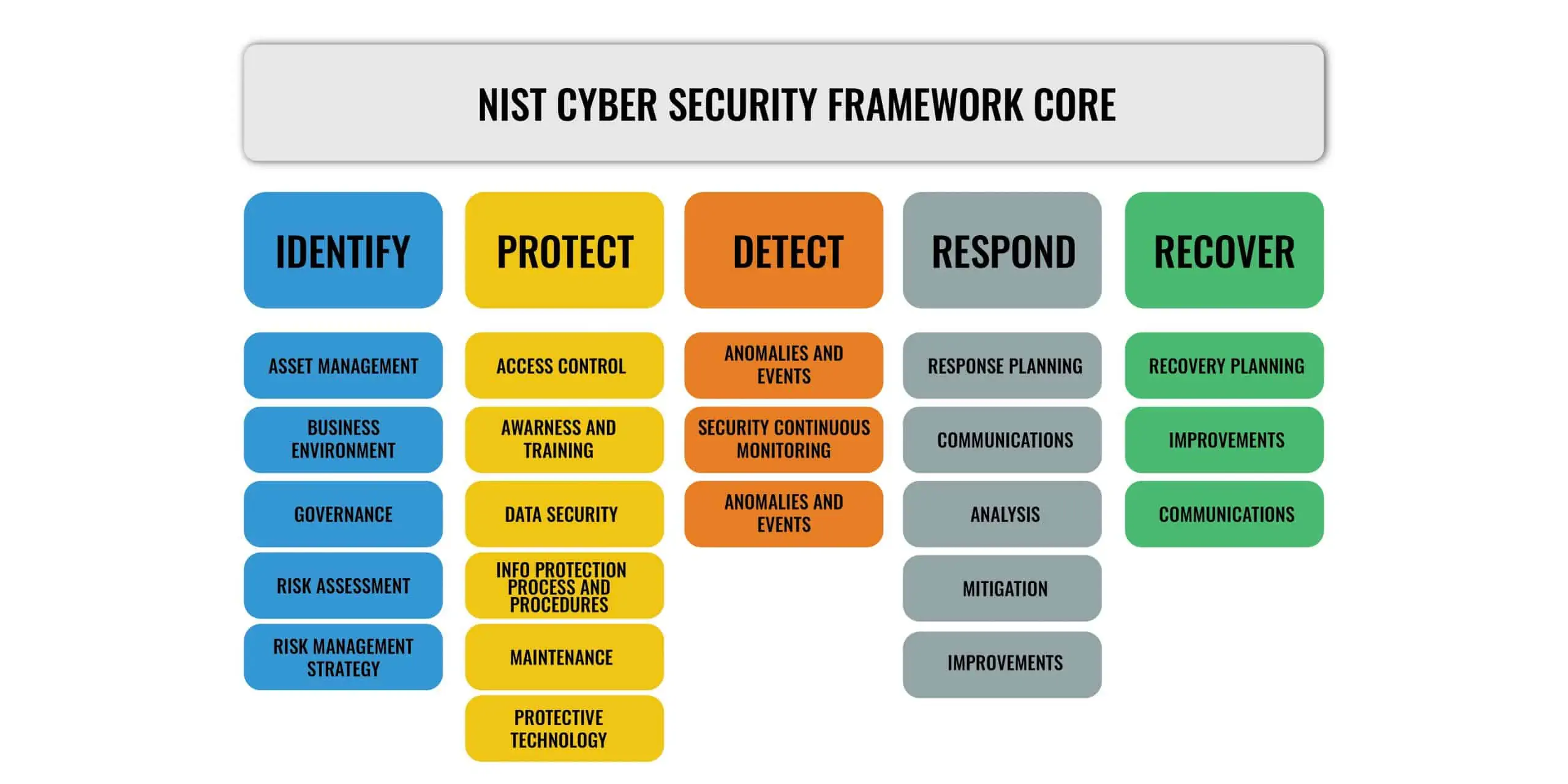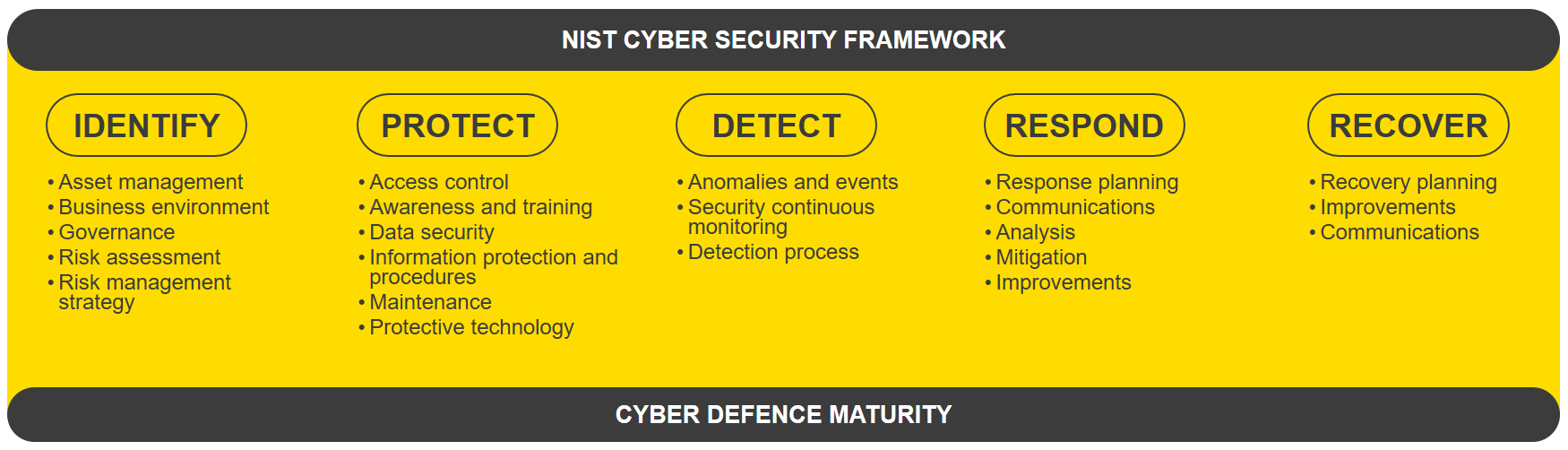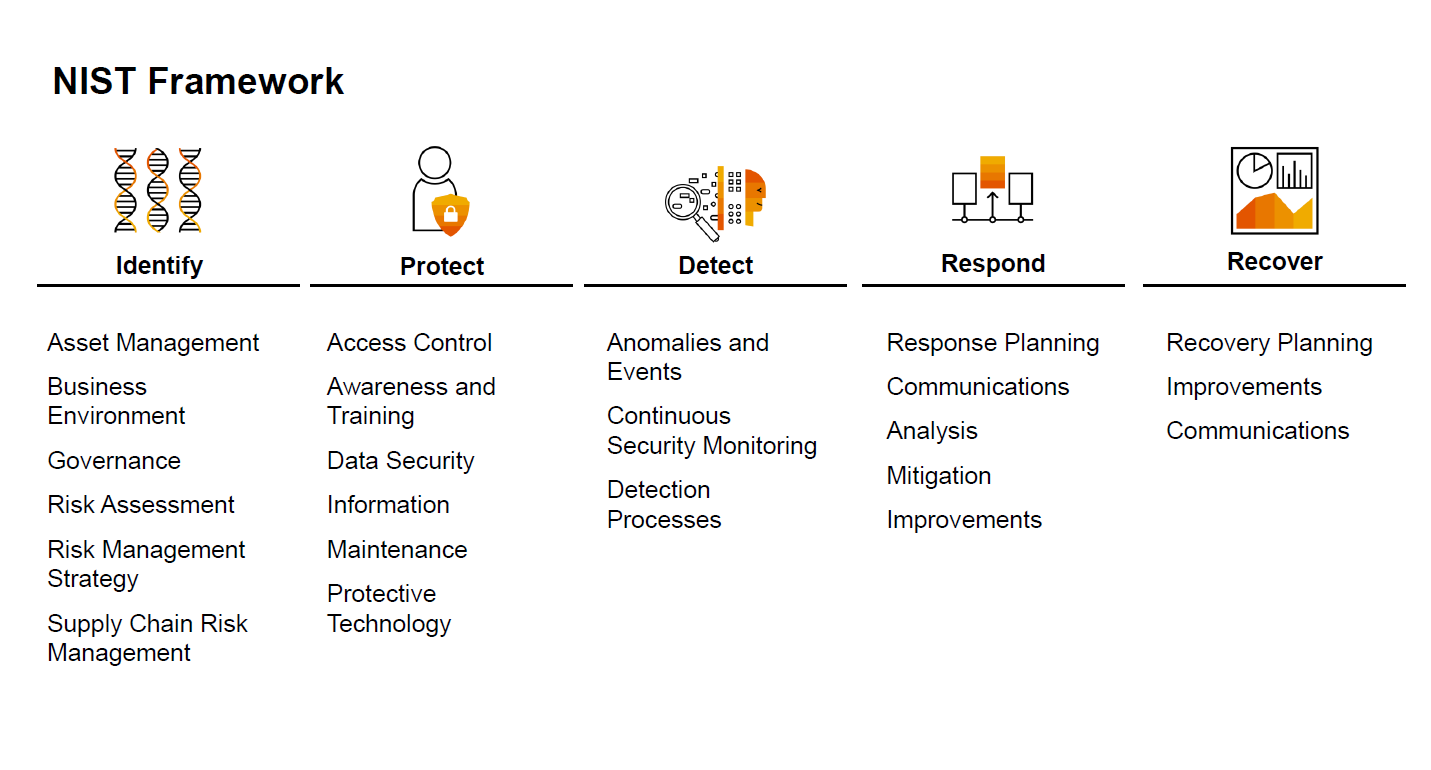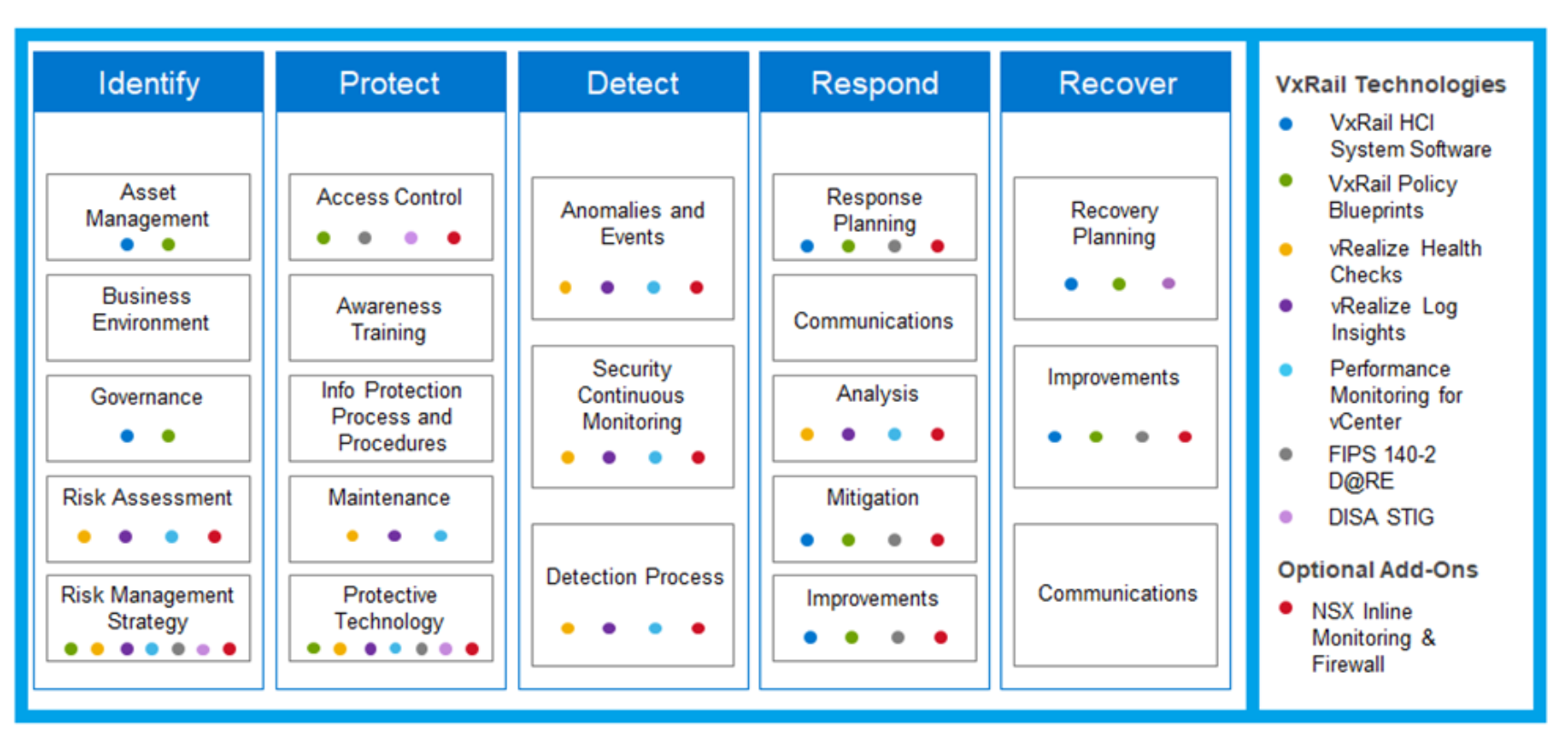
NIST Cybersecurity Framework and VxRail | Dell VxRail: Comprehensive Security by Design | Dell Technologies Info Hub
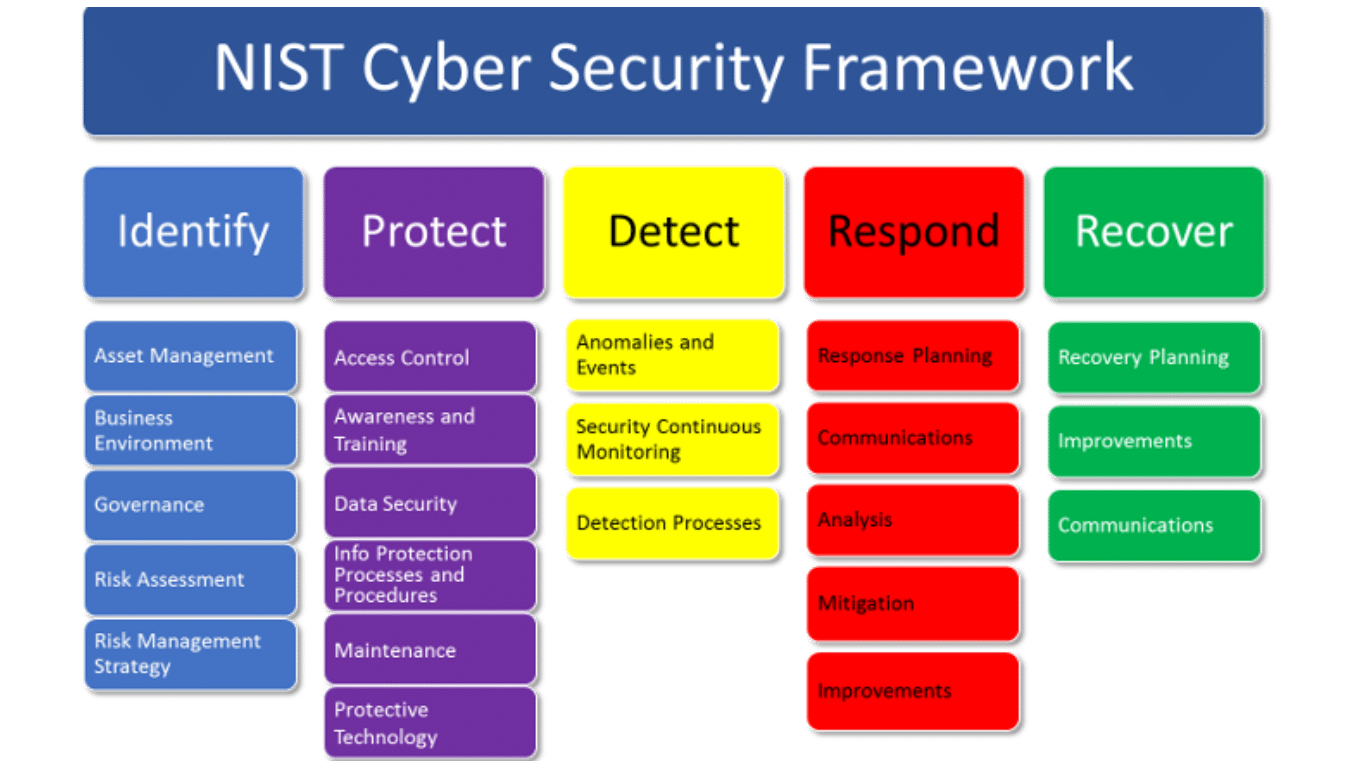
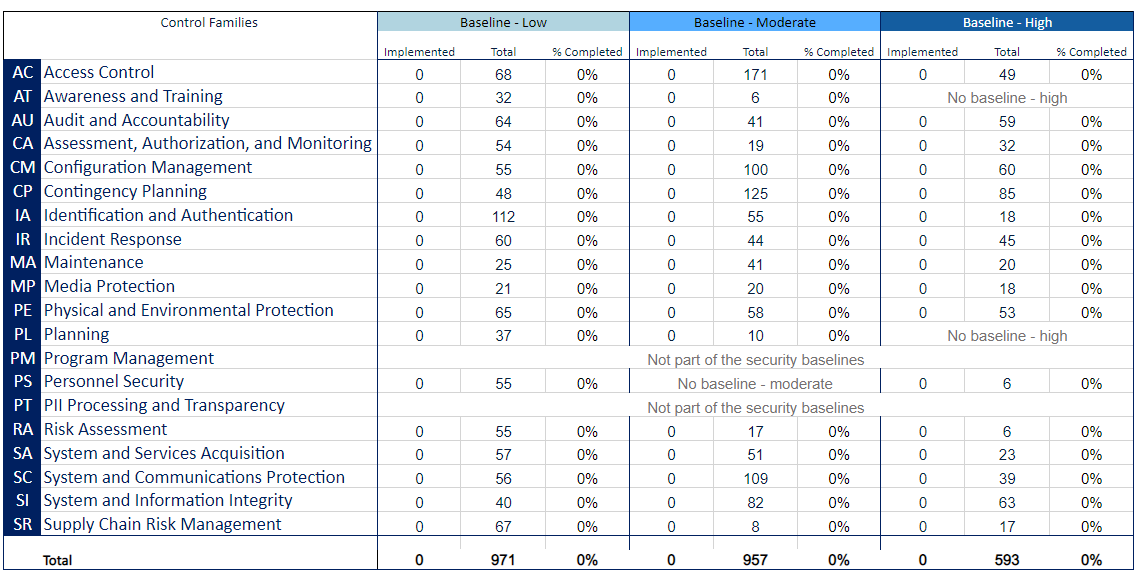
Enhancing NIST Regulation Compliance: Leveraging Continuous Controls Monitoring for Success | Quod Orbis

Information Security Risk & Continuous Monitoring: NIST 800-39, 800-30 rev 1, 800-37 rev 1, & 800-137 : National Institute of Standards & Technology: Amazon.de: Bücher

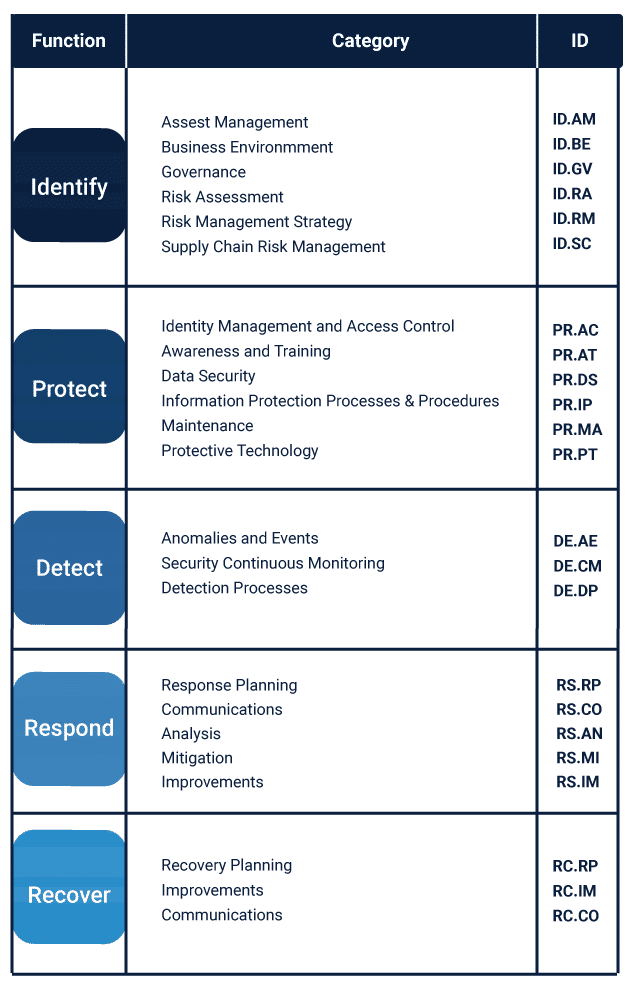
Blockchain Security Monitoring process based on the NIST Cybersecurity... | Download Scientific Diagram