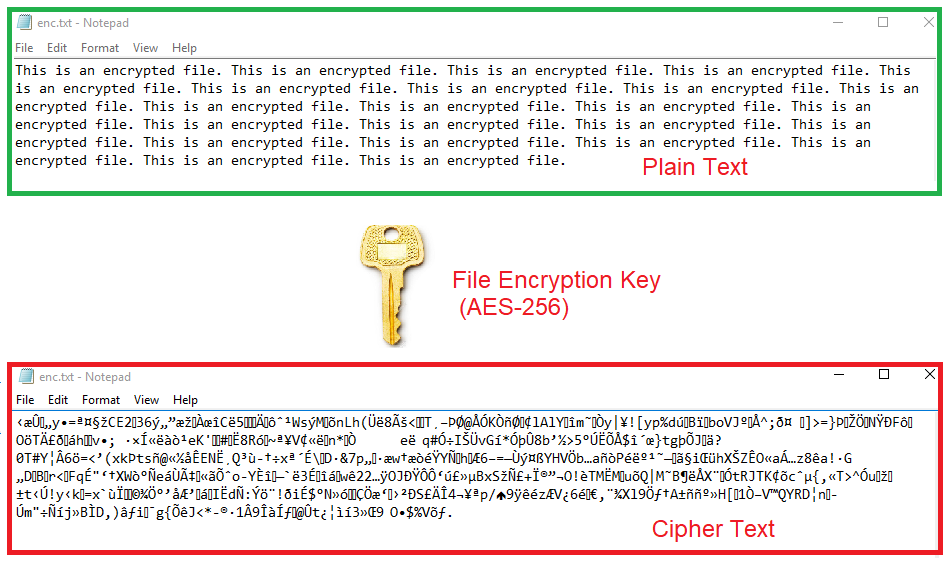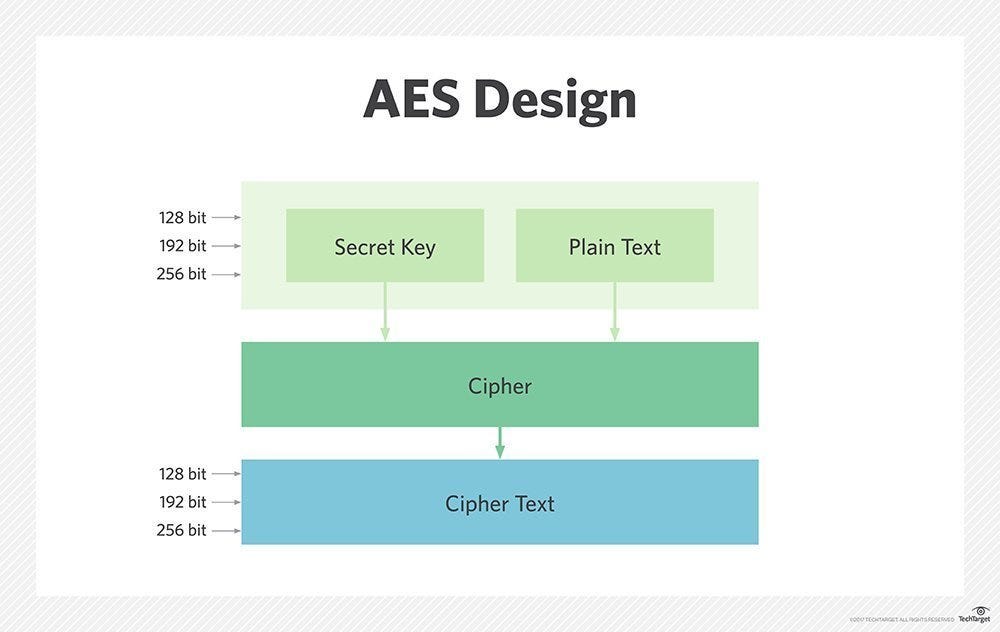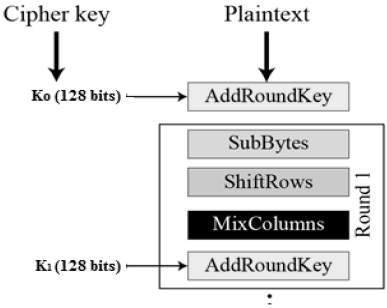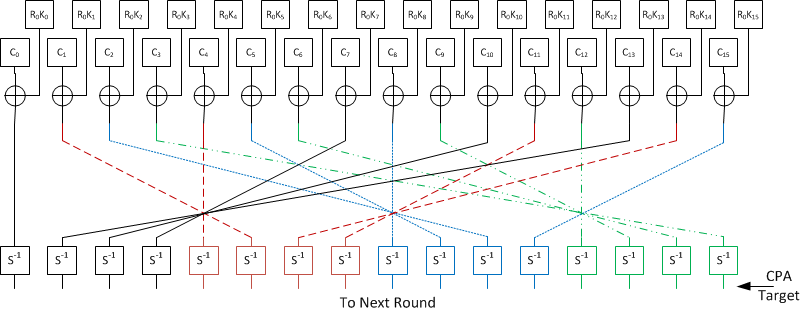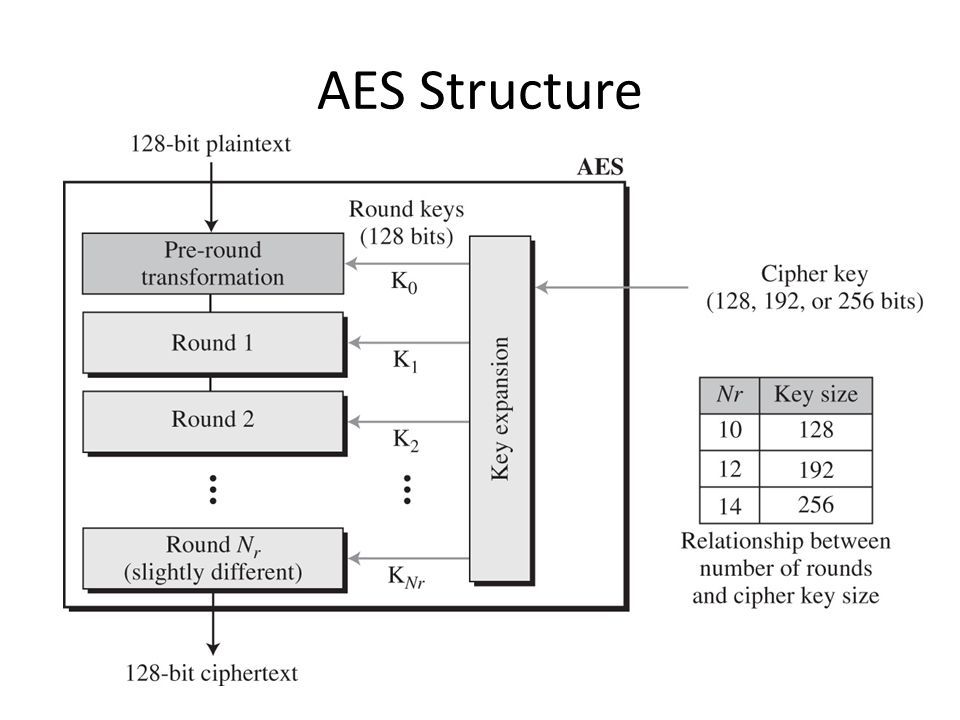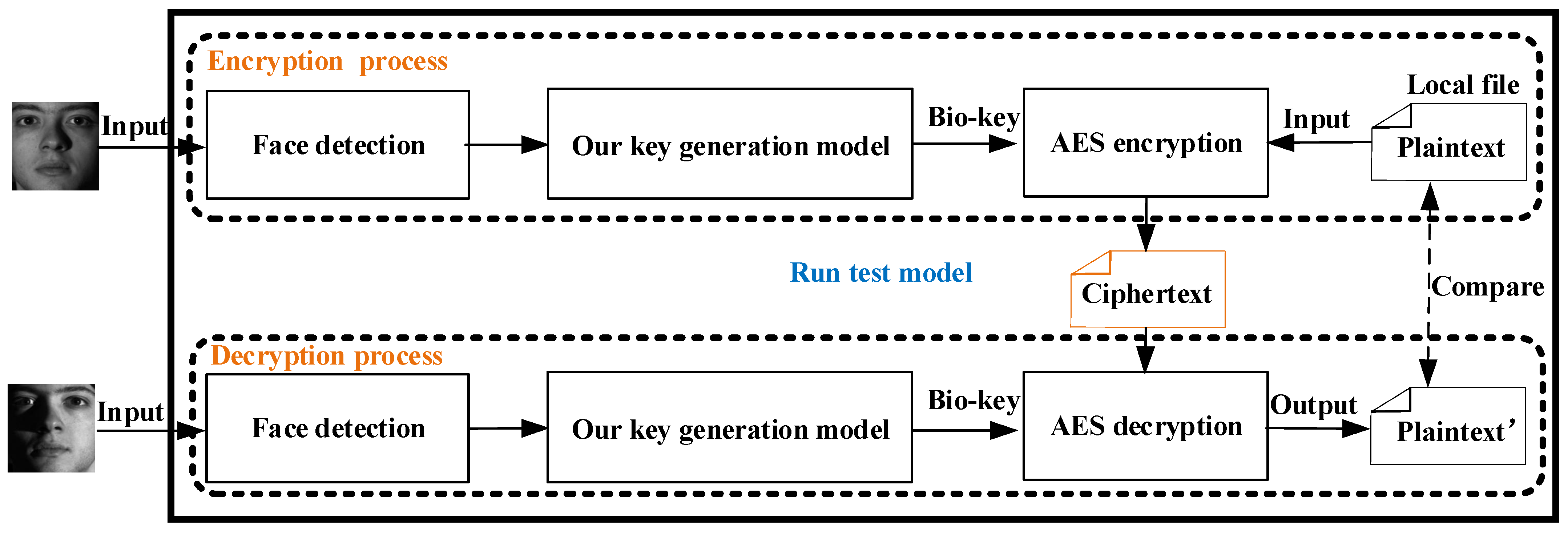
Applied Sciences | Free Full-Text | A Secure Biometric Key Generation Mechanism via Deep Learning and Its Application
Link Key generation Encryption keys: The encryption key is generated... | Download Scientific Diagram
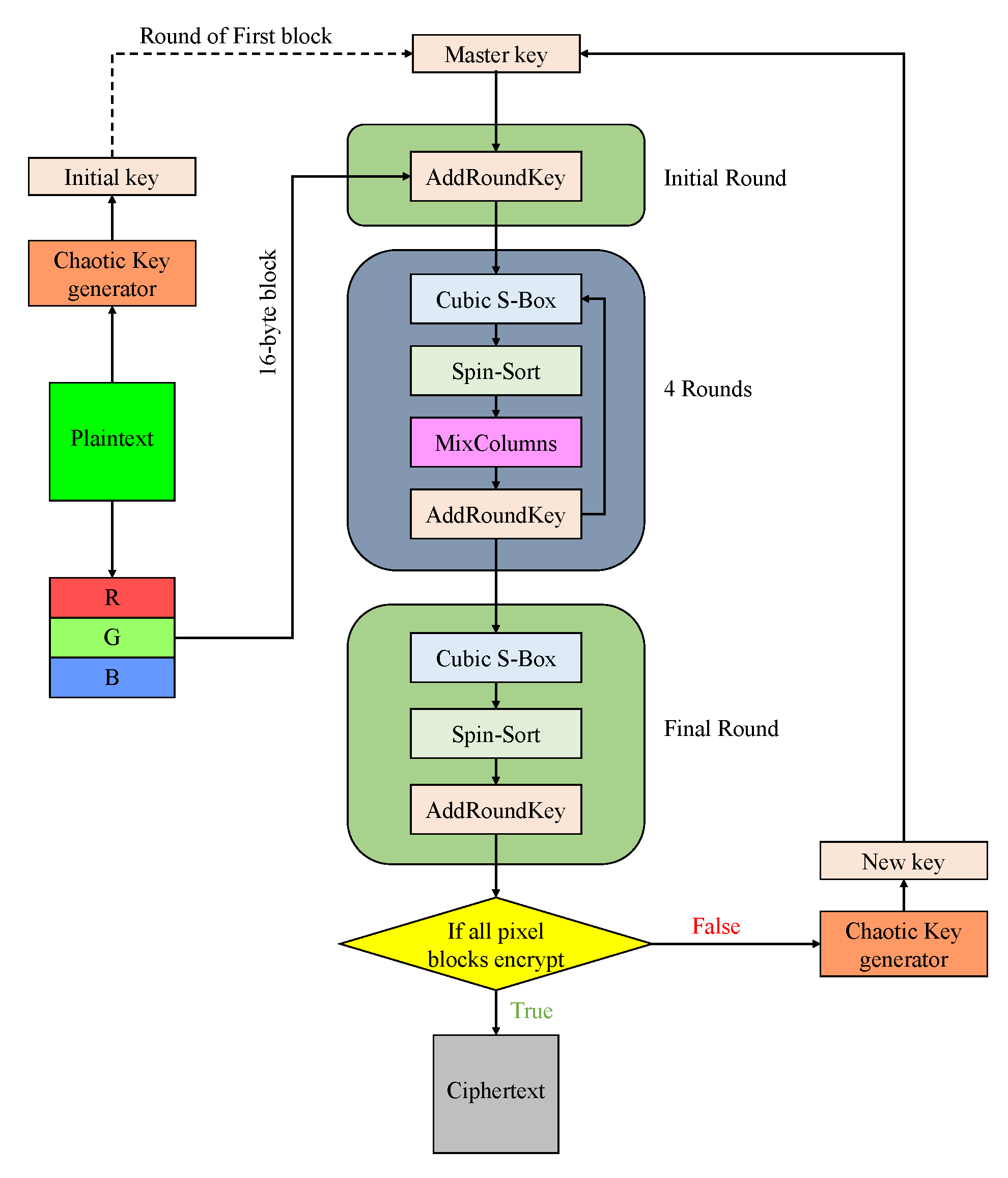
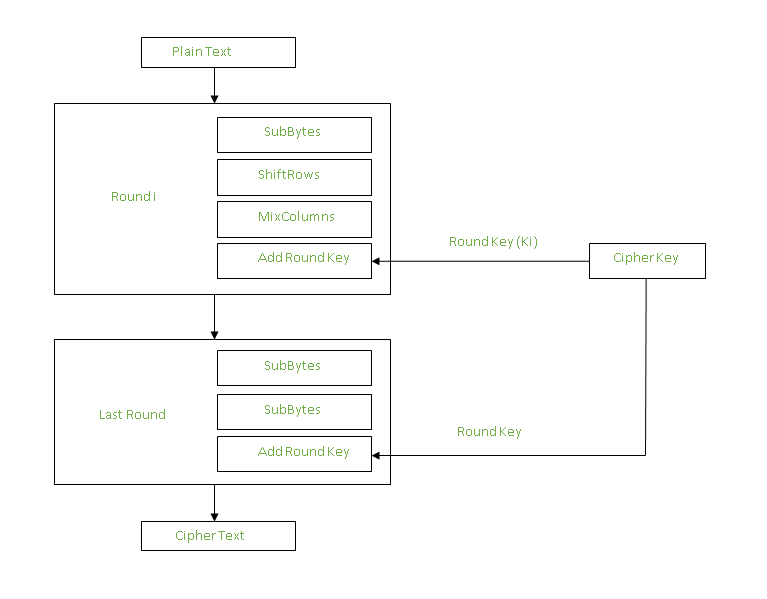
Symmetry | Free Full-Text | FPGA Implementation and Design of a Hybrid Chaos-AES Color Image Encryption Algorithm

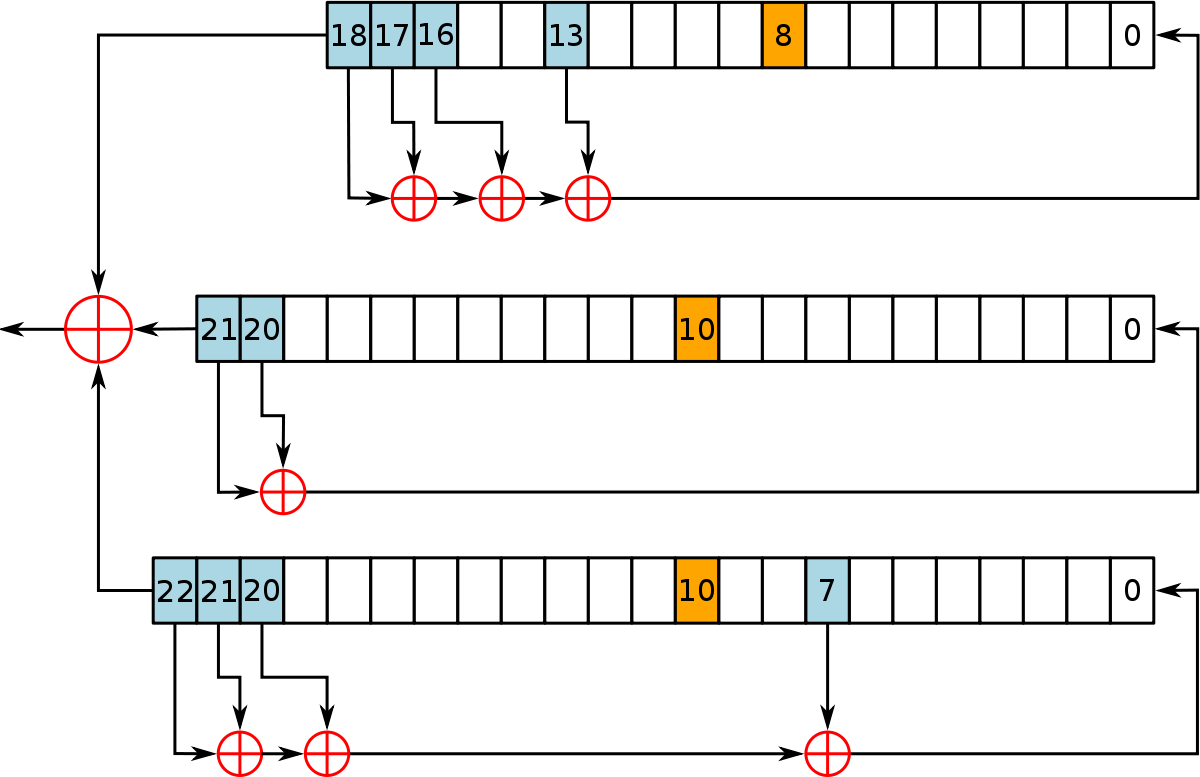
Applied Sciences | Free Full-Text | Omega Network Pseudorandom Key Generation Based on DNA Cryptography

Hybrid Encryption Model Based on Advanced Encryption Standard and Elliptic Curve Pseudo Random | IntechOpen

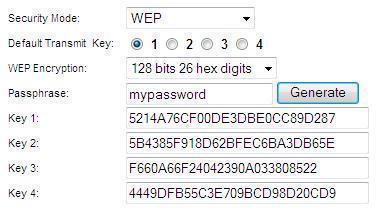
encryption - How does GRC password generator get 512 bit of secret data? - Cryptography Stack Exchange